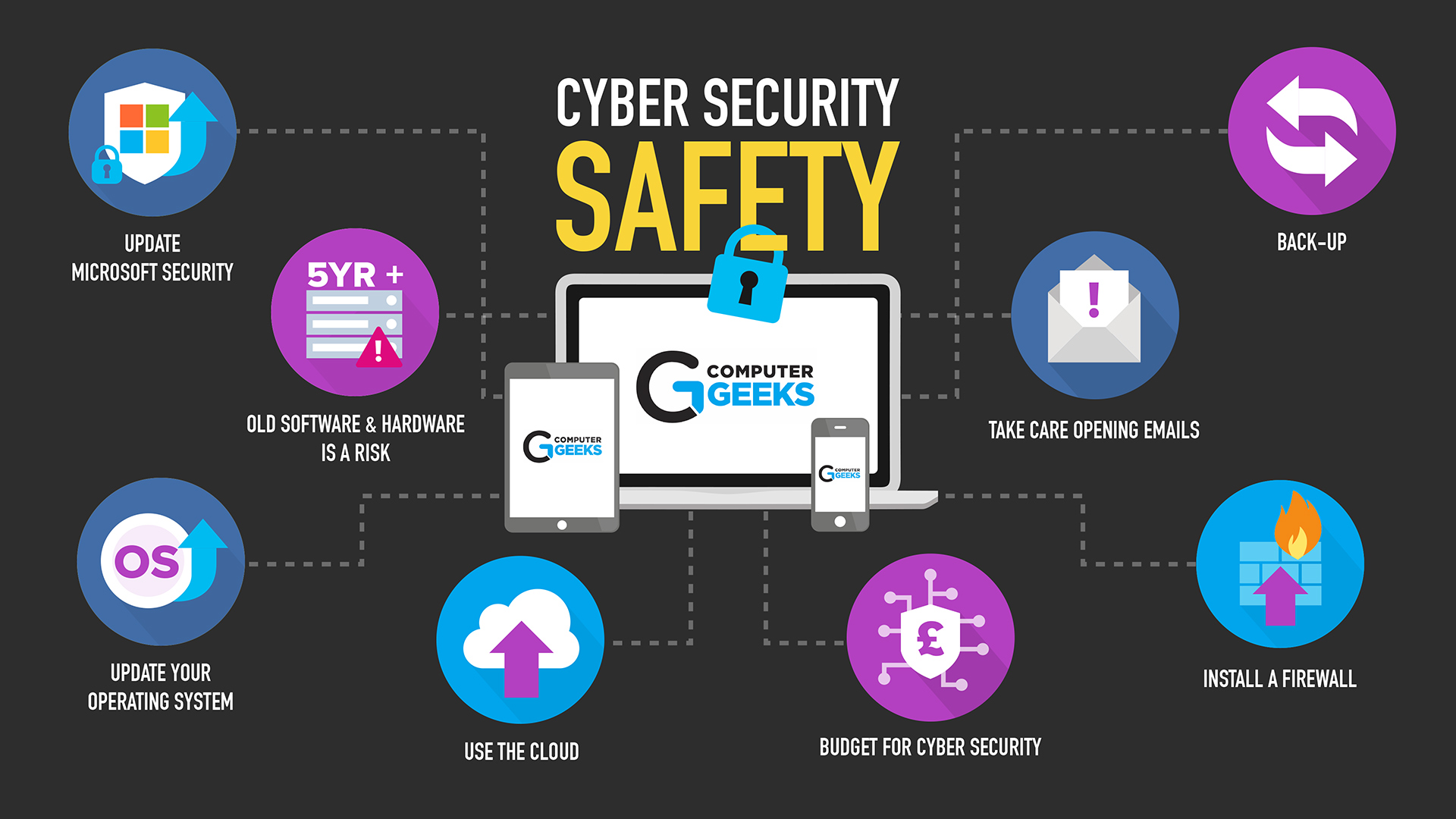
In today's digital age, cyber threats are as ubiquitous as the air we breathe. Imagine your business as a fortress, and cyber threats as relentless invaders seeking to breach your defenses. Just as you wouldn't leave your fortress unguarded, you shouldn't leave your business vulnerable to cyber attacks. So, how do you protect your business from cyber threats? Let's dive in and explore the essential cybersecurity measures you need to implement.
Understanding the Cyber Threat Landscape
Before we delve into the specifics of safeguarding your business, it's crucial to understand the terrain. Cyber threats come in various forms, from phishing emails and ransomware to sophisticated hacking attempts. Each of these threats can cause significant damage, from financial loss to reputational harm. Understanding the landscape helps you tailor your security solutions effectively.
Implementing Robust Cybersecurity Measures
Establishing a Strong Defense
The first line of defense in your cybersecurity strategy is a robust set of security solutions. This includes firewalls, antivirus software, and encryption tools. Think of these as the moat and drawbridge protecting your fortress. They help prevent unauthorized access and protect your sensitive data.
Employee Training and Awareness
Your employees are both your greatest asset and your biggest vulnerability. Regular training sessions on cybersecurity measures can turn them into a formidable defense force. Teach them how to recognize phishing emails, the importance of strong passwords, and the dangers of clicking on suspicious links. Remember, an informed employee is a protected employee.
Regular Updates and Patches
Software updates and patches are like the maintenance crew of your fortress. They fix vulnerabilities and strengthen your defenses. Ensuring that all your software is up-to-date is a critical part of your cybersecurity strategy. Ignoring updates is like leaving a window open in your fortress—it's an invitation for trouble.
Effective Risk Management
Conducting Risk Assessments
Regular risk assessments are essential for identifying potential vulnerabilities in your system. Think of it as a thorough inspection of your fortress, looking for any weak points that need reinforcement. This proactive approach helps you stay one step ahead of potential threats.
Developing a Response Plan
Even the best defenses can be breached. Having a comprehensive response plan in place ensures that you can quickly mitigate the damage and get back on your feet. This plan should include steps for threat detection, containment, and recovery. It's your emergency protocol for when the invaders breach your walls.
Advanced Threat Detection
Utilizing AI and Machine Learning
Advanced threat detection tools, powered by AI and machine learning, can identify and neutralize threats in real-time. These tools are like the sentinels of your fortress, always on the lookout for any suspicious activity. They can detect patterns and anomalies that might otherwise go unnoticed.
Regular Security Audits
Conducting regular security audits is like having a team of inspectors constantly checking the integrity of your fortress. These audits help you identify any gaps in your security measures and ensure that your defenses are up to date.
Investing in Security Solutions
Choosing the Right Tools
Investing in the right security solutions is crucial for safeguarding your business. This includes everything from advanced firewalls to intrusion detection systems. Think of these tools as the arsenal of your fortress, each serving a specific purpose in your defense strategy.
Partnering with Cybersecurity Experts
Partnering with cybersecurity experts can provide you with the specialized knowledge and resources needed to protect your business. These experts are like the elite guard of your fortress, offering advanced training and strategic advice.

Staying Informed and Adaptable
Keeping Up with Industry Trends
The cyber threat landscape is constantly evolving, and so should your security measures. Staying informed about the latest trends and threats helps you adapt your strategies accordingly. Think of it as constantly updating your fortress's blueprint to counter new threats.
Engaging with the Cybersecurity Community
Engaging with the cybersecurity community can provide valuable insights and support. Joining forums, attending conferences, and participating in webinars can help you stay ahead of the curve. It's like having a network of allies who share information and strategies to protect against common enemies.
Conclusion
Safeguarding your business from cyber threats is not a one-time task but an ongoing commitment. By implementing robust cybersecurity measures, conducting regular risk assessments, and staying informed about the latest threats, you can build a fortress that stands strong against any invader. Remember, the key to effective cybersecurity is a combination of proactive measures, advanced tools, and continuous adaptation.
So, are you ready to fortify your business against cyber threats? The journey may seem daunting, but with the right strategies and tools, you can turn your business into an impenetrable fortress.
FAQs
What are the most common types of cyber threats? The most common types of cyber threats include phishing, ransomware, malware, and denial-of-service (DoS) attacks. Each of these threats can cause significant damage to your business.
How often should I update my software? You should update your software as soon as updates become available. Regular updates help fix vulnerabilities and strengthen your defenses against cyber threats.
What is the importance of employee training in cybersecurity? Employee training is crucial because employees are often the first line of defense against cyber threats. Informed employees can recognize and avoid potential threats, reducing the risk of a breach.
What should a cybersecurity response plan include? A cybersecurity response plan should include steps for threat detection, containment, and recovery. It should also outline roles and responsibilities, communication protocols, and procedures for reporting incidents.
How can I stay informed about the latest cyber threats? You can stay informed by following industry news, attending cybersecurity conferences, and joining online communities and forums. Engaging with the cybersecurity community can provide valuable insights and support.

By taking these steps, you can significantly enhance your business's cybersecurity posture and protect it from the ever-evolving landscape of cyber threats. Stay vigilant, stay informed, and stay secure.
Posting Komentar