In today's digital age, cyber threats are as ubiquitous as the internet itself. Imagine your business as a fortress, and cyber threats as relentless invaders seeking to breach your walls. Just as you wouldn't leave your fortress unguarded, you shouldn't leave your business vulnerable to cyber attacks. So, how do you protect your business from cyber threats? Let's dive in and explore the essential cybersecurity measures you need to implement.
Understanding the Cyber Threat Landscape
Before we delve into the how, let's understand the what. Cyber threats come in various forms, from phishing emails and ransomware to data breaches and distributed denial-of-service (DDoS) attacks. Each of these threats can compromise your business's data, reputation, and financial health. According to the Ponemon Institute, the average cost of a data breach in 2021 was \$4.24 million. Can your business afford to take that hit?
Essential Cybersecurity Measures
Implementing Robust Cybersecurity Policies
The first line of defense against cyber threats is a well-crafted cybersecurity policy. Think of it as the blueprint for your fortress's defenses. Your policy should outline clear guidelines for employees, including password management, email usage, and remote work protocols. The National Institute of Standards and Technology (NIST) provides excellent resources for creating comprehensive cybersecurity policies.
Employee Training and Awareness
Your employees are both your strongest asset and your weakest link. A single click on a malicious email can open the gates to a full-scale cyber attack. Regular training sessions can transform your employees into vigilant guardians. Teach them how to spot phishing emails, the importance of strong passwords, and the dangers of public Wi-Fi. Remember, an informed employee is a secure employee.
Regular Software Updates and Patches
Outdated software is like a rusty lock on your fortress's door—easy to pick. Cybercriminals exploit vulnerabilities in outdated software to gain unauthorized access. Regularly updating your software and applying security patches is a simple yet effective way to bolster your defenses. Automate updates whenever possible to ensure nothing slips through the cracks.
Strong Password Management
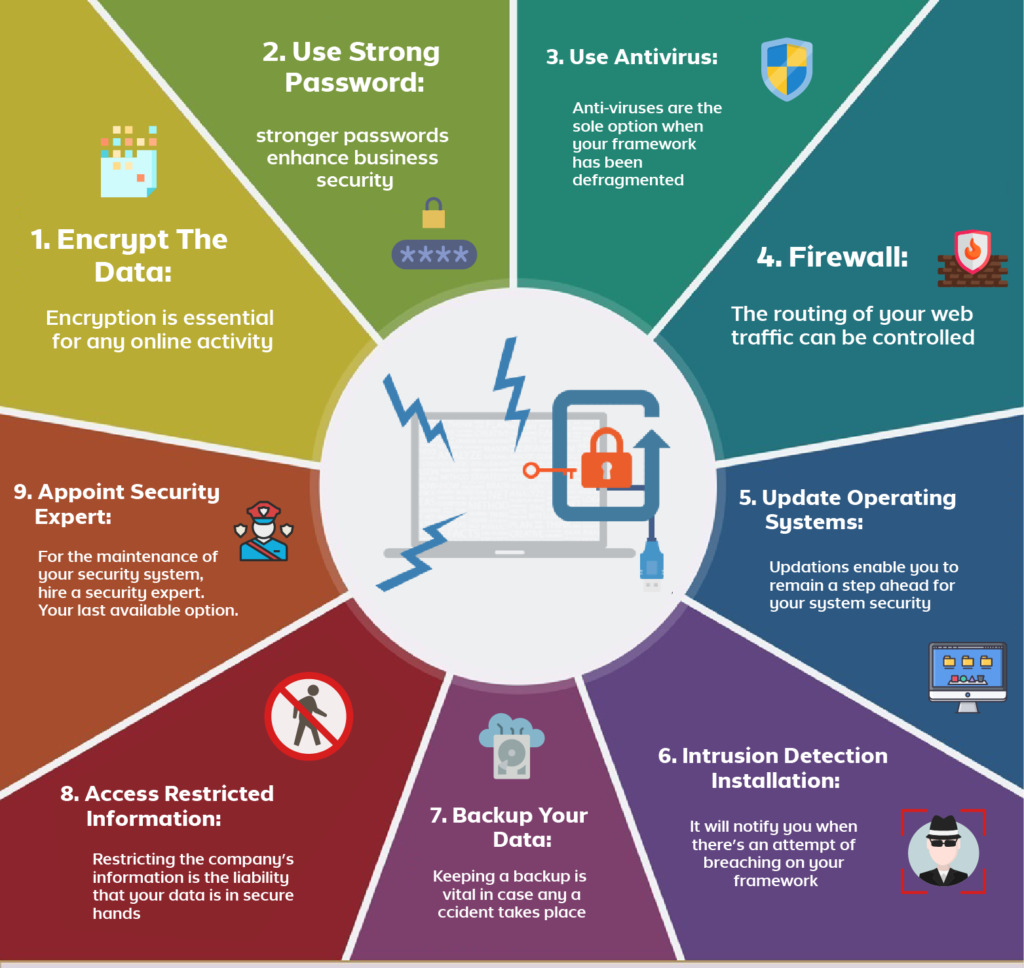
Weak passwords are like leaving the keys to your fortress under the doormat. Implement strict password policies that require complex, unique passwords for all accounts. Encourage the use of password managers to help employees keep track of their credentials securely. Multi-factor authentication (MFA) adds an extra layer of security, making it harder for cybercriminals to gain access.
Data Encryption
Encryption is like a secret language that only you and your trusted allies understand. It scrambles your data, making it unreadable to anyone without the decryption key. Encrypt sensitive data both at rest and in transit to protect it from prying eyes. Tools like BitLocker and VeraCrypt can help you implement robust encryption practices.
Threat Detection and Response
Even the strongest fortress can be breached. That's why threat detection and response are crucial. Implement monitoring tools that can detect unusual activity and alert you to potential threats. Incident response plans should be in place to quickly contain and mitigate any breaches. The Cybersecurity and Infrastructure Security Agency (CISA) offers valuable resources for developing effective incident response plans.
Risk Management Strategies
Conducting Regular Risk Assessments
Risk assessments are like inspecting your fortress for weak points. Regularly evaluate your cybersecurity posture to identify vulnerabilities and areas for improvement. Use frameworks like the NIST Cybersecurity Framework to guide your assessments and prioritize your efforts.
Implementing a Layered Security Approach
A layered security approach is like having multiple walls around your fortress. Each layer adds an additional barrier that cybercriminals must overcome. Combine firewalls, intrusion detection systems, antivirus software, and other security measures to create a comprehensive defense strategy.
Third-Party Risk Management
Your business doesn't operate in a vacuum. Third-party vendors and partners can introduce new risks. Conduct thorough due diligence on all third parties to ensure they meet your cybersecurity standards. Regularly review and update agreements to address evolving threats.
Staying Ahead of Evolving Threats
Cyber threats are constantly evolving, like an ever-changing battlefield. Staying informed about the latest threats and trends is essential for maintaining a strong defense. Subscribe to cybersecurity newsletters, attend industry conferences, and join professional organizations to stay ahead of the curve.
Conclusion
Protecting your business from cyber threats is an ongoing battle. By implementing robust cybersecurity measures, conducting regular risk assessments, and staying informed about evolving threats, you can build a fortress that stands strong against cyber attacks. Remember, cybersecurity is not a one-time project but a continuous journey. Stay vigilant, stay informed, and stay secure.
FAQs
-
What are the most common types of cyber threats? Common cyber threats include phishing, ransomware, data breaches, DDoS attacks, and malware. Each of these threats can compromise your business's data and operations.
-
How often should I update my cybersecurity policies? Cybersecurity policies should be reviewed and updated at least annually. However, significant changes in your business operations or the threat landscape may necessitate more frequent updates.
-
What is multi-factor authentication (MFA), and why is it important? MFA is a security process that requires users to provide two or more forms of identification before accessing an account. It adds an extra layer of security, making it harder for cybercriminals to gain unauthorized access.
-
How can I train my employees to recognize phishing emails? Regular training sessions can help employees recognize phishing emails. Teach them to look for suspicious email addresses, unexpected attachments, and urgent or threatening language. Encourage them to report any suspicious emails to your IT department.
-
What should I do if my business experiences a data breach? If your business experiences a data breach, immediately activate your incident response plan. Contain the breach, notify affected parties, and conduct a thorough investigation to understand the scope and cause of the breach. Seek professional help if necessary to mitigate the damage and prevent future breaches.


Posting Komentar